what tools and techniques are used to exploit web-based applications and systems
Are you seeking the best penetration testing tool for your needs? We have you covered. Penetration testing tools are software applications used to cheque for network security threats. Each application on this listing provides unique benefits. Easy comparing helps y'all determine whether the software is the correct choice for your business concern. Allow'due south swoop in and discover the latest security software options on the market. Penetration testing, also known as pen testing, means computer securities experts utilise to detect and take advantage of security vulnerabilities in a reckoner awarding. These experts, who are too known as white-lid hackers or ethical hackers, facilitate this by simulating real-world attacks by criminal hackers known as black-hat hackers. In effect, conducting penetration testing is similar to hiring security consultants to effort a security attack of a secure facility to find out how real criminals might practise information technology. The results are used past organizations to make their applications more secure. Start, penetration testers must learn about the computer systems they will be attempting to breach. And then, they typically use a set of software tools to find vulnerabilities. Penetration testing may also involve social technology hacking threats. Testers will try to gain admission to a system by tricking a member of an organization into providing access. Penetration testers provide the results of their tests to the organization, which are then responsible for implementing changes that either resolve or mitigate the vulnerabilities. Penetration testing tin can consist of one or more of the post-obit types of tests: A white box test is one in which organizations provide the penetration testers with a variety of security information relating to their systems, to help them better discover vulnerabilities. A bullheaded exam, known as a blackness-box test, organizations provide penetration testers with no security information about the organisation being penetrated. The goal is to expose vulnerabilities that would not exist detected otherwise. A double-blind test, which is as well known equally a covert test, is one in which not only exercise organizations non provide penetration testers with security information. They also do not inform their ain computer security teams of the tests. Such tests are typically highly controlled past those managing them. An external test is one in which penetration testers attempt to notice vulnerabilities remotely. Considering of the nature of these types of tests, they are performed on external-facing applications such as websites. An internal test is 1 in which the penetration testing takes identify within an system's premises. These tests typically focus on security vulnerabilities that someone working from within an arrangement could take reward of. Netsparker Security Scanner is a popular automated spider web application for penetration testing. The software can identify everything from cross-site scripting to SQL injection. Developers can utilise this tool on websites, web services, and spider web applications. The system is powerful enough to scan anything between 500 and 1000 spider web applications at the same time. You lot will be able to customize your security browse with attack options, authentication, and URL rewrite rules. Netsparker automatically takes advantage of weak spots in a read-merely way. Proof of exploitation is produced. The impact of vulnerabilities is instantly viewable. Benefits: Once known as Ethereal 0.2.0, Wireshark is an award-winning network analyzer with 600 authors. With this software, you tin chop-chop capture and translate network packets. The tool is open-source and available for various systems, including Windows, Solaris, FreeBSD, and Linux. Benefits: Metasploit is the almost used penetration testing automation framework in the world. Metasploit helps professional teams verify and manage security assessments, improves awareness, and arms and empowers defenders to stay a stride alee in the game. It is useful for checking security and pinpointing flaws, setting up a defense. An Open source software, this tool will let a network administrator to intermission in and identify fatal weak points. Beginner hackers use this tool to build their skills. The tool provides a way to replicates websites for social engineers. Benefits: This is a pen testing tool and is all-time suited for checking a web browser. Adapted for combating spider web-borne attacks and could benefit mobile clients. BeEF stands for Browser Exploitation Framework and uses GitHub to locate problems. BeEF is designed to explore weaknesses beyond the client system and network perimeter. Instead, the framework will look at exploitability inside the context of only one source, the spider web browser. Benefits: Passwords are one of the nearly prominent vulnerabilities. Attackers may employ passwords to steal credentials and enter sensitive systems. John the Ripper is the essential tool for countersign cracking and provides a range of systems for this purpose. The pen testing tool is a free open source software. Benefits: Aircrack NG is designed for keen flaws within wireless connections by capturing information packets for an effective protocol in exporting through text files for analysis. While the software seemed abandoned in 2010, Aircrack was updated again in 2019. This tool is supported on diverse OS and platforms with back up for WEP dictionary attacks. It offers an improved tracking speed compared to most other penetration tools and supports multiple cards and drivers. Later on capturing the WPA handshake, the suite is capable of using a password dictionary and statistical techniques to break into WEP. Benefits: Acutenix is an automated testing tool you can utilize to complete a penetration test. The tool is capable of auditing complicated management reports and issues with compliance. The software can handle a range of network vulnerabilities. Acunetix is even capable of including out-of-band vulnerabilities. The advanced tool integrates with the highly enjoyed Effect Trackers and WAFs. With a high-detection charge per unit, Acunetix is one of the manufacture's advanced Cantankerous-site scripting and SQLi testing, which includes sophisticated avant-garde detection of XSS. Benefits: There are two different versions of the Burp Suite for developers. The gratis version provides the necessary and essential tools needed for scanning activities. Or, yous can opt for the second version if you lot need advanced penetration testing. This tool is ideal for checking web-based applications. At that place are tools to map the tack surface and analyze requests betwixt a browser and destination servers. The framework uses Spider web Penetration Testing on the Java platform and is an industry-standard tool used past the majority of data security professionals. Benefits: The Ettercap suite is designed to forestall man in the middle attacks. Using this application, you will be able to build the packets you want and perform specific tasks. The software can send invalid frames and complete techniques which are more difficult through other options. Benefits: W3af web application set on and audit frameworks are focused on finding and exploiting vulnerabilities in all web applications. Three types of plugins are provided for attack, audit, and discovery. The software then passes these on to the audit tool to bank check for flaws in the security. Benefits: Nessus has been used every bit a security penetration testing tool for twenty years. 27,000 companies utilize the application worldwide. The software is one of the almost powerful testing tools on the market with over 45,000 CEs and 100,000 plugins. Ideally suited for scanning IP addresses, websites and completing sensitive data searches. You lot will exist able to use this to locate 'weak spots' in your systems. The tool is straightforward to use and offers accurate scanning and at the click of a button, providing an overview of your network's vulnerabilities. The pen test application scans for open ports, weak passwords, and misconfiguration errors. Benefits: Kali Linux advanced penetration testing software is a Linux distribution used for penetration testing. Many experts believe this is the best tool for both injecting and password snipping. However, you will need skills in both TCP/IP protocol to proceeds the about do good. An open-source project, Kali Linux, provides tool listings, version tracking, and meta-packages. Benefits: SQLmap is an SQL injection takeover tool for databases. Supported database platforms include MySQL, SQLite, Sybase, DB2, Access, MSSQL, PostgreSQL. SQLmap is open-source and automates the process of exploiting database servers and SQL injection vulnerabilities. Benefits: Social applied science is the primary focus of the toolkit. Despite the aim and focus, human being beings are not the target of vulnerability scanners. Benefits: OWASP ZAP (Zed Assail Proxy) is function of the complimentary OWASP community. It is ideal for developers and testers that are new to penetration testing. The project started in 2010 and is improved daily. ZAP runs in a cantankerous-platform environment creating a proxy between the customer and your website. Benefits: Wapiti is an application security tool that allows black box testing. Blackness box testing checks web applications for potential liabilities. During the black box testing process, web pages are scanned, and the testing data is injected to check for any lapses in security. Cain & Abel is platonic for procurement of network keys and passwords through penetration. The tool makes use of network sniffing to detect susceptibilities. Finding the right pen testing software doesn't have to be overwhelming. The tools listed higher up represent some of the best options for developers. Remember ane of the best techniques to defend your It structure is to utilise penetration testing proactively. Appraise your IT security by looking for and discovering issues before potential attackers practice.
What Is Penetration Testing?
How Penetration Tests Work
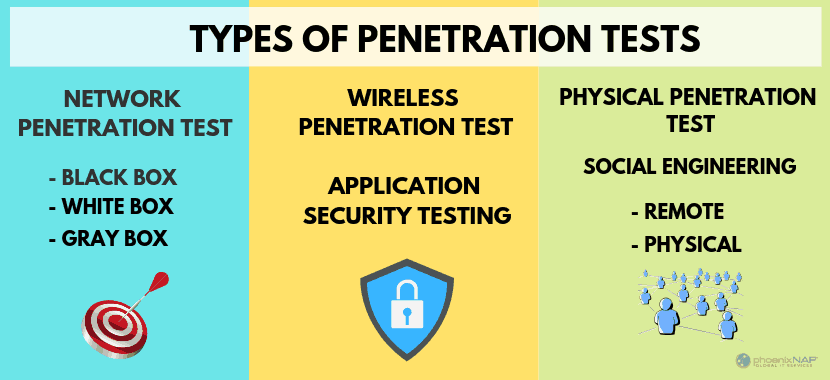
Types of Penetration Tests
White Box Tests
Bullheaded Tests
Double-Blind Tests
External Tests
Internal Tests
Top Penetration Testing Software & Tools
ane. Netsparker
2. Wireshark
3. Metasploit
iv. Beefiness
5. John The Ripper Password Cracker
half dozen. Aircrack
7. Acunetix Scanner
viii. Burp Suite Pen Tester
9. Ettercap
10. W3af
11. Nessus
12. Kali Linux
13. SQLmap
fourteen. (SET) Social Engineer Toolkit
fifteen. Zed Attack Proxy
16. Wapiti
17. Cain & Abel
Get Started with Penetration Testing Software
Goran Jevtic
Goran combines his leadership skills and passion for enquiry, writing, and technology equally a Technical Writing Squad Pb at phoenixNAP. Working with multiple departments and on various projects, he has adult an extraordinary understanding of cloud and virtualization technology trends and best practices.
Source: https://phoenixnap.com/blog/best-penetration-testing-tools
0 Response to "what tools and techniques are used to exploit web-based applications and systems"
ارسال یک نظر